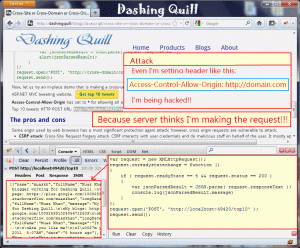
We can initiate cross-domain request in our webpage by creating either XMLHttpRequest object or XDomainRequest object. End user’s web-browser will request data from the domain’s server by sending an “Origin” header with the value of origin. If server responds with an “Access-Control-Allow-Origin:* | Origin” then we are permitted to access data; otherwise response will be unauthorized request.
Because we’ve to handle our server response for allowing cross-origin requests; we’ll use BeginRequest event handler in the Global.asax file for adding “Access-Control-Allow-Origin” header in our response.
HttpApplication.BeginRequest event occurs as the first event in the HTTP pipeline chain of execution when ASP.NET responds to a request. The BeginRequest event signals the creation of any given new request. This event is always raised and is always the first event to occur during the processing of a request.
protected void Application_BeginRequest(object sender, EventArgs e)
{
HttpContext.Current.Response.AddHeader(
"Access-Control-Allow-Origin", "*"); /* HttpContext.Current.Response.AddHeader(
"Access-Control-Allow-Origin",
"http://AllowedDomain.com"); */
}
Asterisk (*) symbol indicates that request is public; however for the sake of security; we can allow a specific domain. In that case, the server will check whether request’s “Origin” header matches with domain-name that we allowed. So server will block unauthorized requests as soon as possible.
You can validate requests action-level by creating an attribute inherited to “ActionFilterAttribute” and allow only one action method to be accessible from cross-domains.
Support of Cross Browsers
Cross-Origin requests supported on IE8 (Windows 7 version),
Safari 4+, Chrome and Firefox 3.5+ web-browsers. Preflight or Credential requests are supported on Firefox 3.5+, Safari 4+ and Chrome web-browsers; IE8 doesn’t support them. You’ve to use XDomainRequest object for supporting IE8+ for cross-origin requests. IE6 and IE7 are not
supporting cross-origin requests.
For more details: please read Nicholas C. Zakas‘s article: Cross-domain Ajax with Cross-Origin Resource Sharing
Possible Attacks
Same origin used by web browsers
has a most significant protection again attack; however, cross origin requests are mostly vulnerable to attack.
- CSRF attack: Cross-Site Request Forgery attack. CSRF interacts
with user credentials and do malicious stuff on behalf of the user. It mostly applied to email accounts. - XSS attack: Cross-Site Scripting attack occurs to inject malicious
data with POST/GET messages. - DNS Rebinding attack is interaction with DNS hostnames and networks address. Hacker injects malicious code and executes it; on the server side; server consider hacker’s request as authentic request because hostname matches.
- Spoofing and re-direction attacks are mostly applied
to cross-origin requests because server heavily relies upon HTTP headers to determine which site can access resources as well as what action they are permitted to do.
For cross-origin requests’ security: “Ensure user authority cannot be misused or compromised“.
A while ago, I wrote an article “ASP.NET MVC security and hacking: Defense-in-depth“, in which I talked about XSS and CSRF attacks. All of those attacking techniques also apply to cross-origin requests.
There is no definitive way to protect your cross-origin requests however; you can make your requests harder to attack by using some techniques as Google,
Twitter and Facebook are doing with their cross-origin APIs like Twitter‘s tweets APIs; Facebook‘s live stream and comments APIs.

You must be logged in to post a comment.